- Home
- Security & Compliance
- Secure and govern workloads with network-level segmentation🔓
Secure and govern workloads with network-level segmentation🔓
Unlocking Secure Connectivity a Comprehensive Guide to Azure Network Segmentation & Security
Network segmentation is a strategy where you take your network and break it into software-defined perimeters using tools available in Microsoft Azure. This allows you to create specific rules that control the flow of traffic in and out of these segments. 📊 By doing so, you can apply different security measures to different parts of your network.
When you place various applications—or even parts of the same application—into these segments, you gain the power to control how they communicate with each other. 🔄 If a part of your application stack gets compromised, segmentation can help contain the threat, stopping it from spreading across your entire network. 🚫 This approach is a core principle of the Zero Trust model by Microsoft, which focuses on delivering top-notch security for your organization.
Segmentation Patterns in Azure 🌐
When you’re working on Azure, you’ve got a diverse set of segmentation options to keep your network secure. Here’s a breakdown of the key patterns available to help you protect your workloads:
📂 Subscription
A subscription is a high-level boundary that provides separation between different entities. It’s ideal for dividing large parts of an organization. Resources in separate subscriptions can’t communicate unless you set up specific connections.
🌐 Virtual Network (VNet)
Virtual Networks are private networks within a subscription. By default, there’s no traffic allowed between VNets, giving you strong containment. Like subscriptions, if you need them to communicate, you’ll have to set it up manually.
🔒 Network Security Groups (NSGs)
NSGs are like a layer 4 firewall, controlling traffic within your VNet and to external networks. 🛑 They help you fine-tune your segmentation, allowing you to create security perimeters around subnets, groups of VMs, or even individual VMs.
🛠️ Azure Virtual Network Manager (AVNM)
AVNM allows central IT teams to manage networks across multiple subscriptions. It’s a powerful tool for enforcing security rules at scale. Similar to NSGs, AVNM uses layer 4 firewall controls, but it applies admin security rules first, adding an extra layer of protection.
🏷️ Application Security Groups (ASGs)
ASGs let you manage network security based on application context. You can group VMs under an application tag and apply specific rules to them, making your segmentation strategy even more application-focused.
🔥 Azure Firewall
Azure Firewall is a cloud-native, stateful firewall that acts as a gatekeeper for your traffic. 🚪 It can filter traffic between cloud resources, the Internet, and on-premises networks, using rules from layer 3 to layer 7. It’s a great choice for comprehensive traffic control, and you can even leverage third-party security providers for advanced filtering.
📊 Common Patterns for Azure Network Segmentation
When it comes to organizing your workloads in Azure, there are several ways to segment and secure your network. Each pattern offers a different type of isolation and connectivity, so choosing the right one depends on your organization’s unique needs.
Remember, there’s no one-size-fits-all solution! You might combine several approaches to create a custom fit for your organization. Azure gives you the flexibility and tools to design a network that works best for you.
Pattern 1: Single Virtual Network
In this pattern, all the components of your workload—or even your entire IT environment—are housed within a single virtual network (VNet). This setup works best if you’re operating in a single region, as a VNet can’t stretch across multiple regions. 🌍
To segment this virtual network, you’ll likely use Network Security Groups (NSGs) or Application Security Groups (ASGs):
- NSGs are great if you want to define segments using network subnets. 🌐
- ASGs are ideal if you prefer to organize by application groups. 🏷️
Below is an example of what a segmented virtual network might look like:
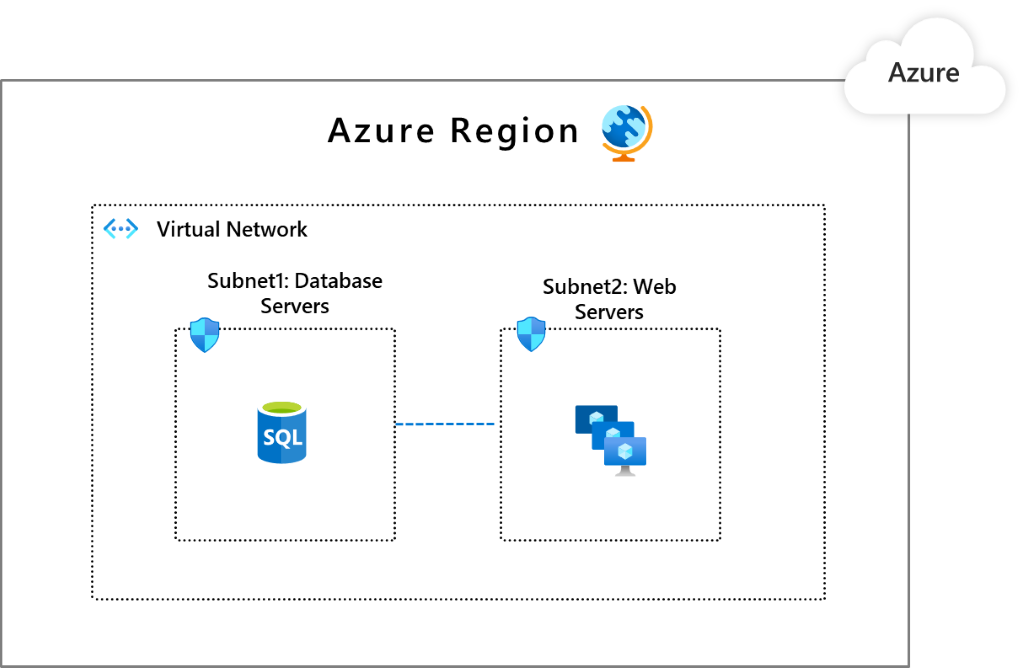 Image Credits to Microsoft Docs
Image Credits to Microsoft Docs
In this setup:
- Subnet1 is where you place your database workloads. 🗄️
- Subnet2 hosts your web workloads. 🌐
With NSGs, you can set rules like:
- Allow Subnet1 to communicate only with Subnet2. 🔄
- Allow Subnet2 to access the Internet, but restrict other traffic. 🌍❌
As your environment grows and more workloads are added, you can create subnets that restrict communication, ensuring one workload can’t access another’s backend. 🔒 This adds a powerful layer of protection by keeping sensitive areas isolated.
While we used NSGs for this example, you can also achieve the same segmentation using a Network Virtualized Appliance from the Azure Marketplace or by deploying an Azure Firewall. 🔥 These tools provide even more control over traffic and security, giving you flexibility in how you protect your network.
Pattern 2: Multiple Virtual Networks with Peering
This pattern is an extension of the single VNet setup. Here, you have multiple virtual networks (VNets) that can be connected through peering. You might choose this pattern to:
- Group applications into separate VNets for better organization. 📦
- Operate in multiple Azure regions, which requires separate VNets. 🌍
One of the advantages of this setup is the built-in segmentation. VNets are isolated by default—you have to set up peering connections if you want them to communicate. 🛡️ Keep in mind, though, that VNet peering isn’t transitive. If VNet A is peered with VNet B, and VNet B is peered with VNet C, A and C won’t automatically connect.
For additional segmentation within each VNet, you can still use NSGs or ASGs just like in the single VNet pattern. This way, you get precise control over how your resources can communicate, even in a multi-VNet environment. 🔄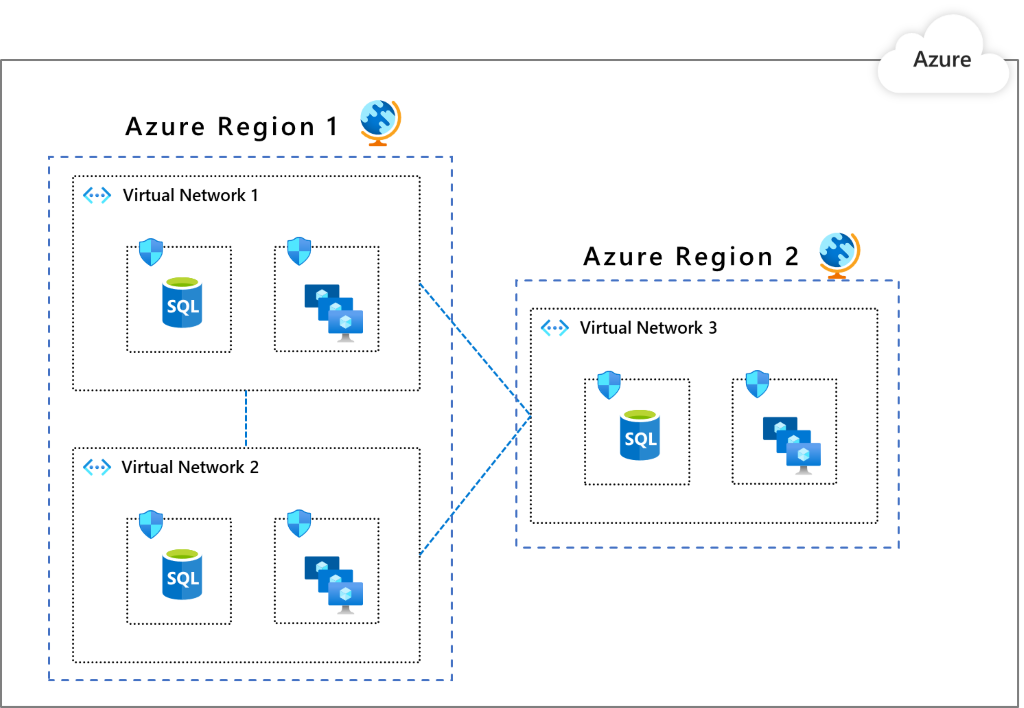 Image Credits to Microsoft Docs
Image Credits to Microsoft Docs
Pattern 3: Multiple Virtual Networks in a Hub and Spoke Model
This pattern is a more advanced network setup in Azure. You select one VNet in a region to act as the hub, while other VNets in that region become the spokes.
How it Works:
- The hub VNet connects to all the spoke VNets using Azure VNet peering. 🔗
- All traffic flows through the hub, which can also serve as a gateway to other hubs in different regions. 🌐
Benefits of the Hub and Spoke Model:
- You set up your security rules at the hub, allowing you to manage and govern traffic between VNets in a scalable way. 🚦
- As your network grows, the security overhead remains low because you only manage policies at the hubs—unless you expand to a new region. 📈
Additionally, this pattern can be upgraded by using Azure Virtual WAN, which offers a managed service for handling a hub VNet. This can make managing complex networks easier and more efficient. 🌟 Check out the Hub-and-Spoke Virtual WAN Architecture for more details on how Azure Virtual WAN can enhance your network. Image Credits to Microsoft Docs
Image Credits to Microsoft Docs
Azure Firewall: The Recommended Cloud-Native Segmentation Control
The go-to solution for network segmentation in Azure is Azure Firewall! (Azure also support 3rd Party next Gen Firewalls Ex. Palo Aalto, Sophos, fortinet, etc) It works seamlessly across both Virtual Networks and subscriptions, using powerful layer 3 to layer 7 controls to govern traffic flows. 🌐
What You Can Do with Azure Firewall:
- Define clear communication rules:
- Example: VNet X can’t communicate with VNet Y, but can talk with VNet Z. 🔄
- Restrict VNet X from Internet access, except for specific sites like
*.github.com. 🌍🔒
- Apply these rules consistently across your environment for a secure setup.
Manage Policies Centrally:
With Azure Firewall Manager, you can centrally handle policies across multiple Azure Firewalls, making it easy to enforce security at scale. 📊 Plus, you can empower your DevOps teams to create and customize local policies as needed. 🛠️
Azure Firewall Manager also integrates seamlessly with Azure Virtual WAN, letting you use it as a managed hub network, adding another layer of simplicity and control for your cloud infrastructure.
Pattern 4: Multiple Virtual Networks Across Multiple Network Segments
In this pattern, you manage and protect multiple virtual networks spread across different network segments and subscriptions—all in a centralized way. 🏢🔗
How It Works:
- Use Azure Virtual Network Manager (AVNM) to enforce security admin rules across your entire network. 🚦
- These rules apply consistently, no matter if the virtual networks are connected or if they belong to separate subscriptions.
Example Use Case:
- You can create a rule to disable high-risk ports like:
- SSH (Port 22) 🛑
- RDP (Port 3389) 🚫
- This adds a strong layer of protection against security breaches across all virtual networks in your organization. 🔒
To learn more about these rules and how they work, check out Security Admin Rules in Azure Virtual Network Manager.
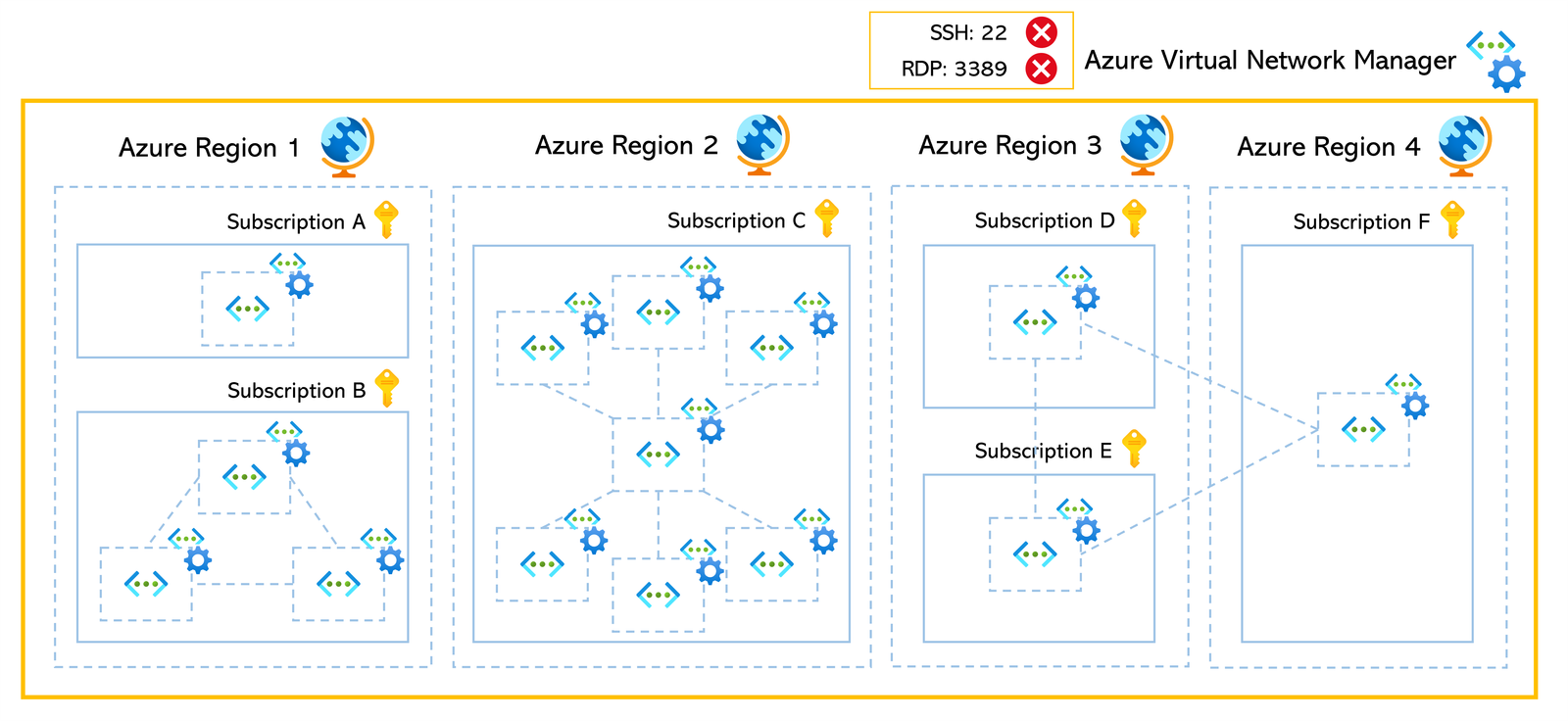 Image Credits to Microsoft Docs
Image Credits to Microsoft Docs
While Azure Virtual Network Manager (AVNM) is fantastic for setting up broad network protection with a minimum set of security rules, you’ll still need to use Network Security Groups (NSGs) and Application Security Groups (ASGs) for more detailed control over each virtual network. 🕵️♂️
Why Use NSGs and ASGs?
- AVNM covers your entire network with baseline security rules, but…
- NSGs and ASGs allow you to apply fine-grained rules tailored to specific systems or workloads. 📋
Customizing for Your Needs:
This layered approach can vary from system to system, depending on each one’s unique security requirements. By combining AVNM with NSGs and ASGs, you get a flexible and secure setup that meets the demands of your organization. 🔧🔒
What is Azure Virtual WAN? 🚀
Azure Virtual WAN is a powerful networking service that combines multiple networking, security, and routing functions into a single, easy-to-manage platform. 🛠️ It’s designed to simplify and streamline your network operations.
Key Features of Azure Virtual WAN:
- Branch Connectivity 📡: Seamlessly connect branches using Virtual WAN Partner devices like SD-WAN or VPN CPE.
- Site-to-Site VPN 🌍: Connect your on-premises locations securely to Azure.
- Remote User VPN 👩💻👨💻: Allow remote workers to connect securely via point-to-site VPN.
- Private Connectivity 🔒: Use ExpressRoute for private, dedicated connections to Azure.
- Intra-Cloud Connectivity 🌩️: Enable transitive connections between virtual networks.
- VPN and ExpressRoute Integration 🔗: Combine VPN and ExpressRoute for flexible network setups.
- Advanced Routing & Security 🔄🛡️: Manage routing, use Azure Firewall, and encrypt private connections.
Start Small, Scale as Needed
You don’t need to implement every feature right away. Begin with a single use case and adjust your network over time as it grows and evolves. 📈
Hub and Spoke Architecture
Azure Virtual WAN uses a hub and spoke design, offering built-in scale and performance for connecting branches, users, ExpressRoute circuits, and virtual networks. This structure supports a global transit network, allowing transitive connections between different types of spokes, all managed through a central cloud hub. 🌐🔗
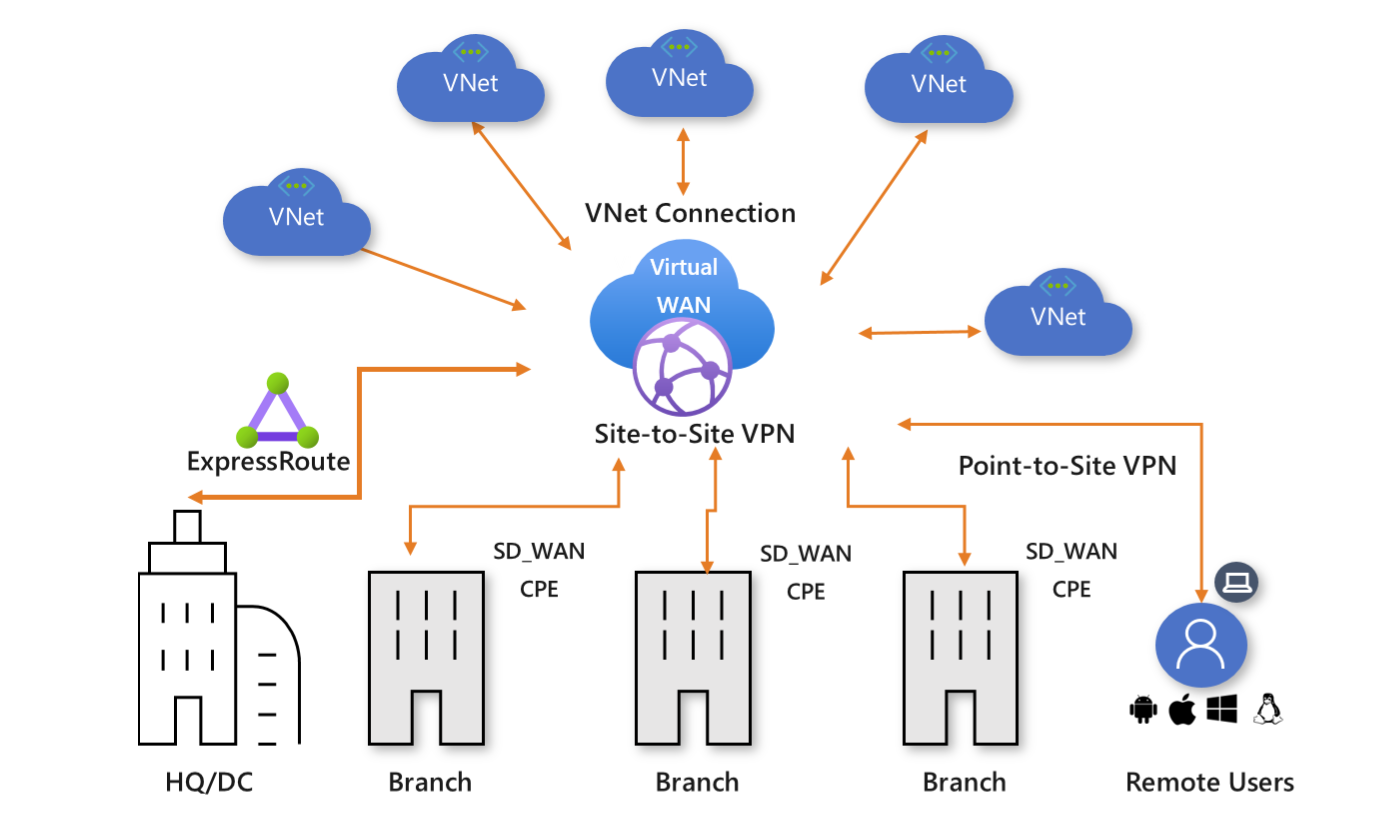 Image Credits to Microsoft Docs
Image Credits to Microsoft Docs

