- Home
- Security & Compliance
- DevSecOps on Azure Kubernetes Service (AKS) Architecture Review👨💻
DevSecOps on Azure Kubernetes Service (AKS) Architecture Review👨💻
DevSecOps on Azure Kubernetes Service (AKS) a Comprehensive Review
Businesses are continually seeking ways to enhance their software development and deployment processes. DevOps has been a cornerstone in this transformation, bridging the gap between development and operations. However, as security threats grow more sophisticated, integrating security into the DevOps pipeline—commonly referred to as DevSecOps—has become imperative. This guide delves into how you can leverage DevSecOps practices using Azure Kubernetes Service (AKS) to build and deploy secure, scalable applications.
What is DevSecOps?
DevSecOps integrates security practices within the DevOps process, ensuring that security is a shared responsibility throughout the lifecycle of software development. Instead of bolting security at the end of the development cycle, DevSecOps promotes the concept of “shifting left,” embedding security from the inception of the project.
Why Choose AKS for DevSecOps?
Azure Kubernetes Service (AKS) offers a managed Kubernetes environment, simplifying the deployment and management of containerized applications. It provides robust features to implement DevSecOps, including:
- Scalability and High Availability: AKS automatically handles tasks such as health monitoring and maintenance, providing a scalable and resilient platform.
- Integration with Azure Security: AKS integrates seamlessly with Azure’s security tools, offering a secure foundation for running containerized applications.
- Compliance: Azure provides comprehensive compliance coverage, helping organizations meet their regulatory requirements.
Architecture of DevSecOps on AKS
The architecture for implementing DevSecOps on AKS involves several key components and best practices, depicted in the following diagram:
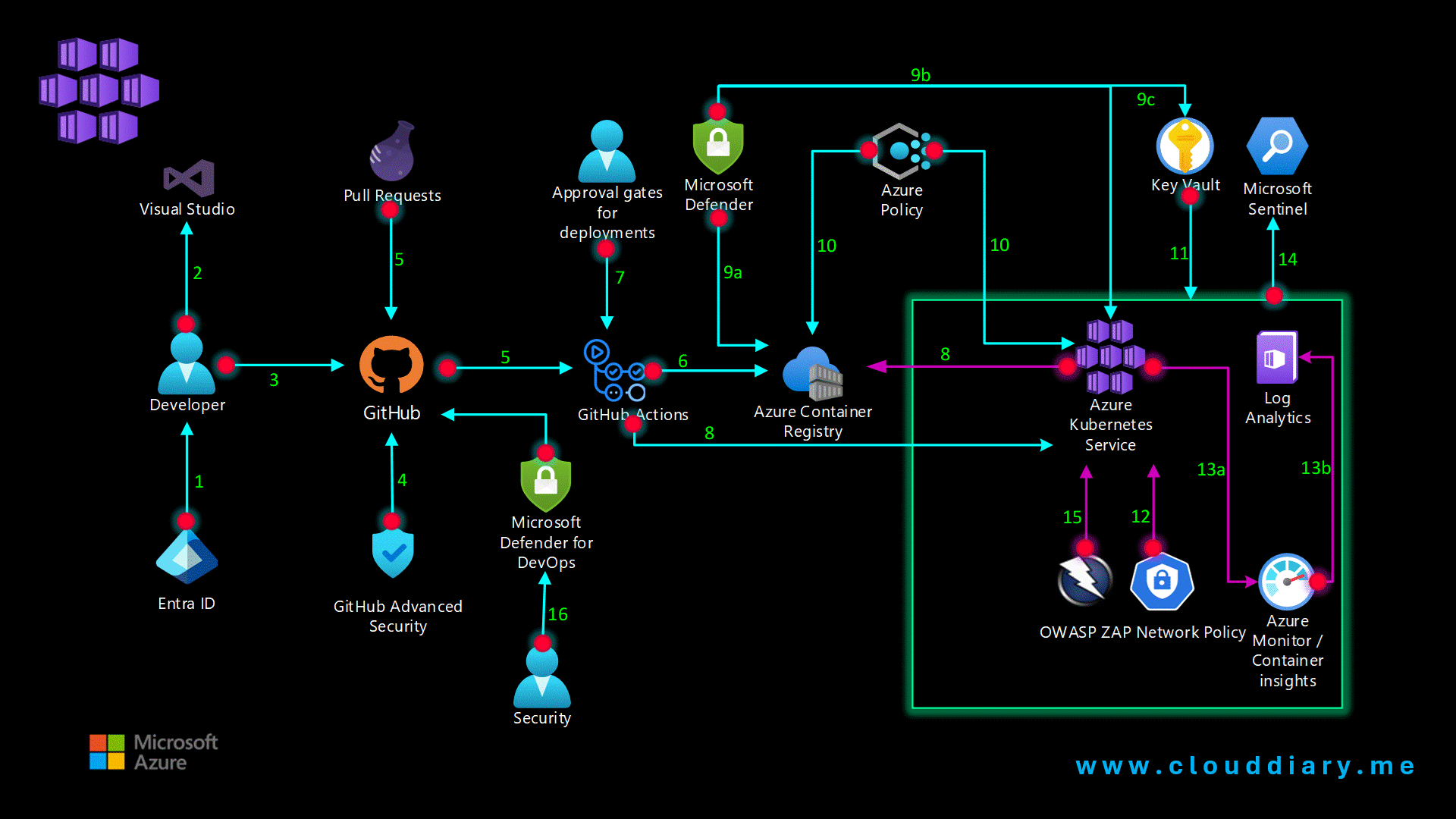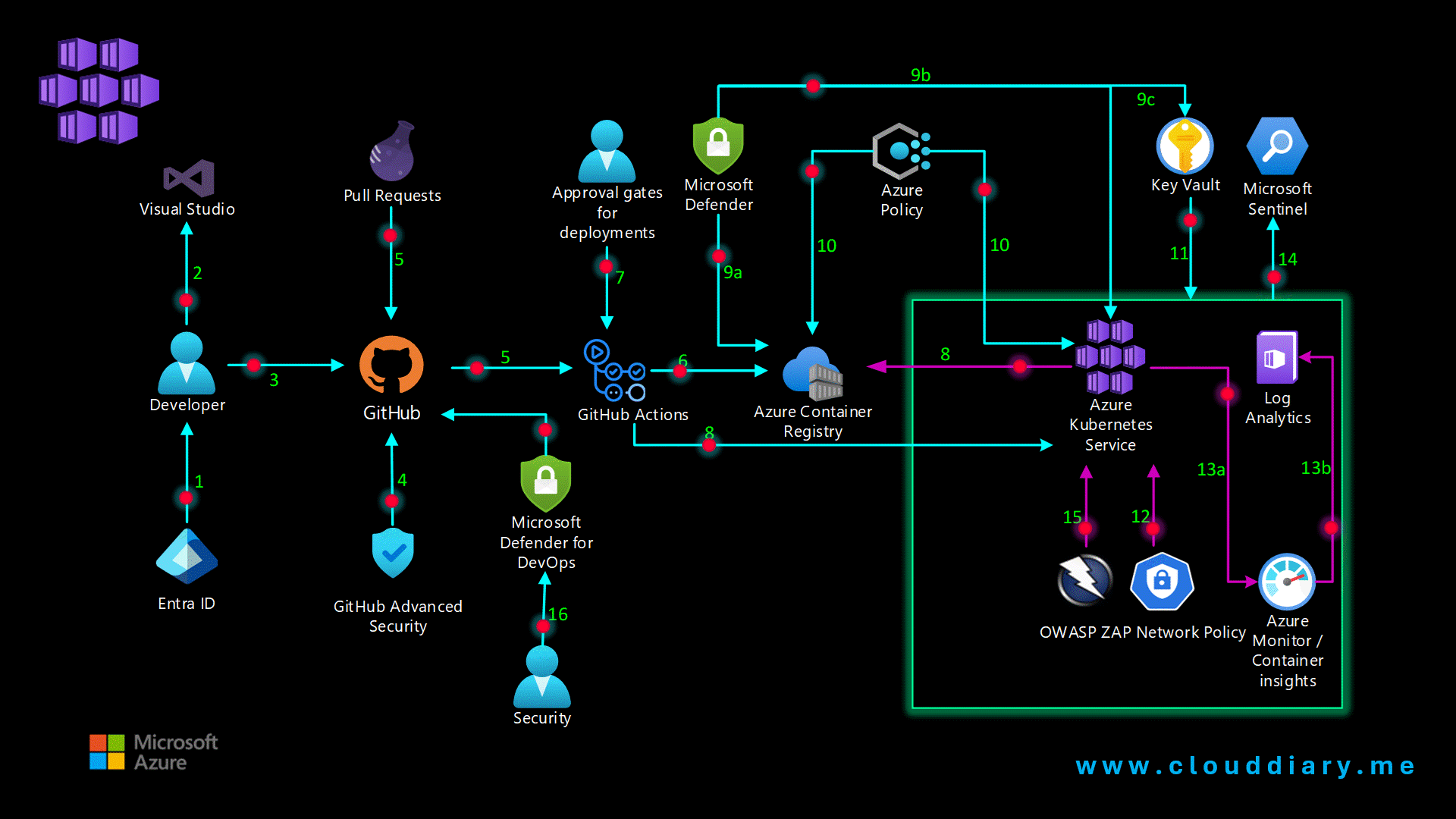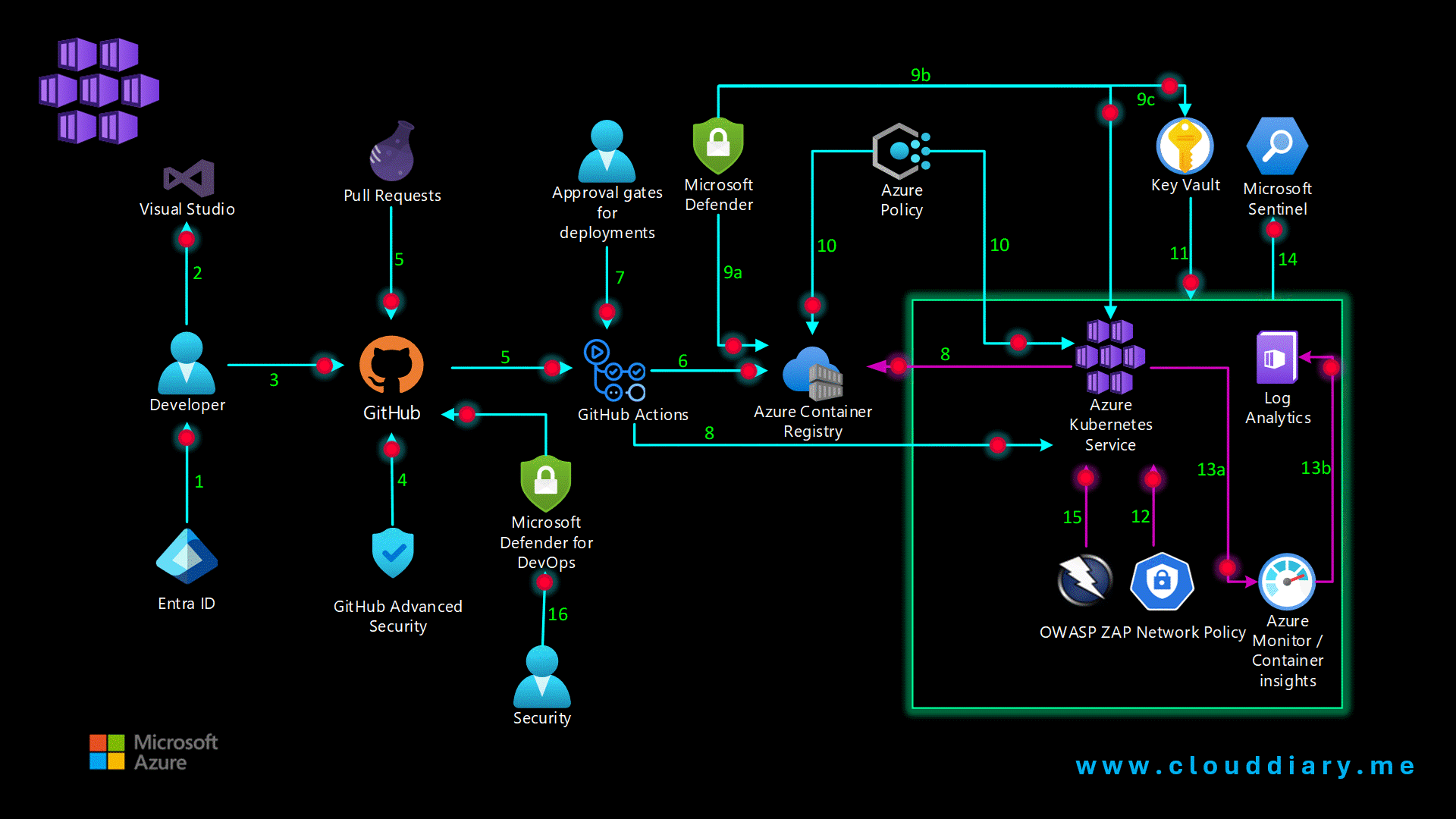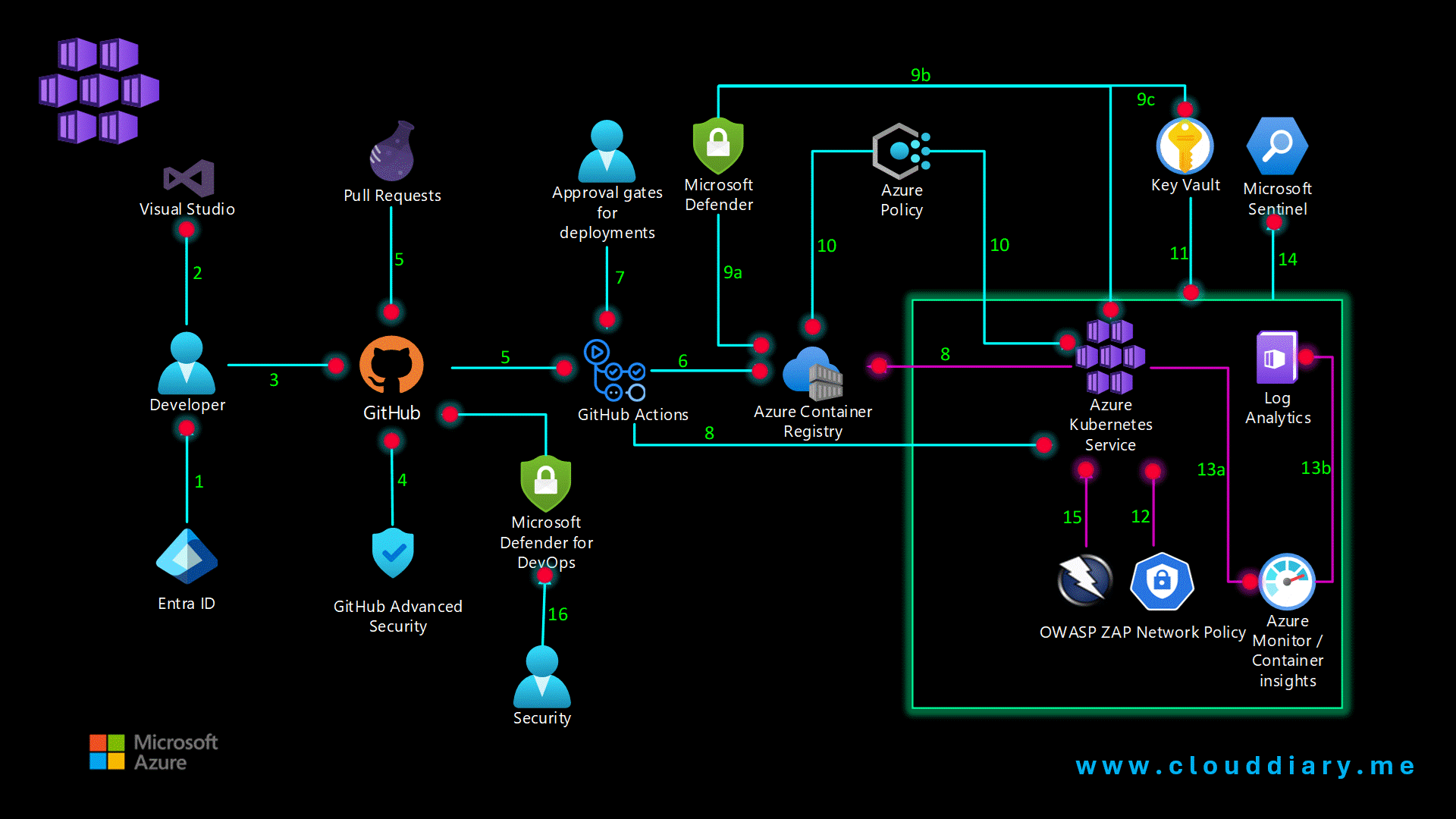
Key Components and Flow Explanation
Identity and Access Management:
- Microsoft Entra ID (formerly Azure Active Directory) is configured as the identity provider for GitHub, ensuring secure user authentication and enabling Multi-Factor Authentication (MFA) for enhanced security.
Development Environment:
- Developers use Visual Studio or VS Code with security extensions enabled. These tools help proactively analyze and secure their code against vulnerabilities during the development phase.
Source Control:
- Application code is committed to a corporate-owned GitHub Enterprise repository. This ensures that the code is securely managed and governed.
Security Scanning:
- GitHub Advanced Security integrates automatic security and dependency scanning into the development process, helping identify potential vulnerabilities early.
CI/CD Pipeline:
- GitHub Actions: Pull requests trigger Continuous Integration (CI) builds and automated testing workflows. This CI pipeline generates Docker container images.
Container Image Storage:
- The Docker container images generated during CI are stored securely in Azure Container Registry (ACR).
Approval Gates:
- As part of the Continuous Delivery (CD) workflow in GitHub Actions, manual approvals can be introduced for deployments to sensitive environments, like production.
Continuous Delivery:
- GitHub Actions also enable Continuous Delivery (CD) to AKS. This process includes security checks to detect secrets, credentials, and other sensitive information within the application source and configuration files.
Security Scanning and Enforcement:
- Microsoft Defender is used to scan for security vulnerabilities across different components:
- 9a: Azure Container Registry – Scans container images for known vulnerabilities when they are uploaded.
- 9b: Azure Kubernetes Service (AKS) – Performs runtime scans and provides threat protection.
- 9c: Azure Key Vault – Monitors for unusual or suspicious attempts to access key vault accounts.
- Microsoft Defender is used to scan for security vulnerabilities across different components:
Policy Compliance and Enforcement:
- Azure Policy is applied to enforce security and compliance policies for ACR and AKS. These policies help ensure that the infrastructure adheres to predefined security standards.
Secret Management:
- Azure Key Vault is used to securely inject secrets and credentials into applications at runtime, ensuring sensitive information is protected and separated from developers.
Network Security:
- AKS Network Policies are configured to secure traffic between application pods. These policies help control and restrict communication within the AKS cluster, enhancing the security of network interactions.
Continuous Monitoring and Log Management:
- 13a: Azure Monitor and Container Insights provide continuous monitoring of the AKS cluster, collecting performance metrics and analyzing application and security logs.
- 13b: Azure Log Analytics aggregates diagnostic and application logs into a workspace where log queries can be executed for detailed analysis.
Security Threat Detection and Response:
- Microsoft Sentinel, a Security Information and Event Management (SIEM) solution, ingests and analyzes logs from the AKS cluster. Sentinel applies defined patterns and rules to detect security threats and initiate appropriate responses.
Application Security Testing:
- OWASP Zed Attack Proxy (ZAP) is an open-source tool used to perform penetration testing on web applications. ZAP identifies vulnerabilities and security gaps that could be exploited by attackers.
Multi-Pipeline Security Management:
- Defender for DevOps is part of Microsoft Defender for Cloud. It empowers security teams to manage DevOps security across multiple CI/CD pipelines, including GitHub and Azure DevOps, providing a unified view and control over security practices.
Best Practices for DevSecOps on AKS
- Shift Security Left: Incorporate security checks and scans early in the development process to catch and fix vulnerabilities before they reach production.
- Automate Security Processes: Implement automated tools and workflows for scanning, testing, and policy enforcement to streamline security and reduce manual errors.
- Continuous Monitoring: Maintain real-time visibility into your environment with tools like Azure Monitor and Sentinel to quickly detect and respond to threats.
- Adopt the Principle of Least Privilege: Limit access to resources and data to the minimum necessary, reducing the risk of unauthorized access.
- Regularly Update and Patch Systems: Keep your software and infrastructure up-to-date with the latest security patches to mitigate known vulnerabilities.
Implementing DevSecOps on Azure Kubernetes Service (AKS) provides a powerful framework for securing applications throughout the development lifecycle. By leveraging Azure’s extensive tools and best practices, organizations can integrate security seamlessly into their DevOps workflows, ensuring robust protection against modern threats. Adopting DevSecOps on AKS not only enhances security but also promotes agility and continuous innovation.


Gopinathan Nagarajan
January 10, 2025Great concept with more details and explanations along with visual format
Anuradha
January 10, 2025Thank you very much