- Home
- Security & Compliance
- Network Segmentation Strategy on Azure🔐
Network Segmentation Strategy on Azure🔐
Network Segmentation Strategy on Azure for Secure and Efficient Virtual Networks
As more organizations move to the cloud, it’s vital to have a strong network segmentation strategy. In this Blog, we’ll break down the basics of network segmentation on Azure and share some best practices to keep your virtual network secure and efficient.
🔐 Why is Network Segmentation Important?
In today’s cybersecurity landscape, it’s wise to assume that breaches can happen. Network segmentation helps contain potential threats, protecting your information systems. By adopting a Zero Trust strategy, which focuses on user, device, and application identities, you can enhance your security and manage risks more effectively. Here are some key benefits:
- Grouping related assets for better management.
- Isolating resources to prevent unauthorized access.
- Meeting compliance and governance requirements.
- Limiting the impact of potential attackers.
Learn More about Secure networks with Zero Trust
🌐 Understanding Azure Virtual Networks
Azure Virtual Networks (VNets) provide private address spaces for your resources. By default, VNets don’t allow traffic between each other, but you can connect them using:
- Virtual network peering – A straightforward way to link VNets.
- An Azure VPN Gateway – Securely connects VNets over the internet.
🌐 Using Subnets for Segmentation
Subnets are smaller networks within a VNet that help you organize and isolate resources. Some subnets have specific purposes, such as:
🌐 Reserved IP Addresses in Subnets
Azure reserves five IP addresses in each subnet for internal use, which include:
- Network address (e.g.,
x.x.x.0) - Default gateway (e.g.,
x.x.x.1) - Azure DNS IPs (e.g.,
x.x.x.2,x.x.x.3) - Network broadcast address (e.g.,
x.x.x.255)
🌐 Security Features in Azure
Azure provides various tools to control and secure your network:
- Network Security Groups (NSGs): Control inbound and outbound traffic at layer 3 and 4.
- Application Security Groups (ASGs): Simplify NSG management by grouping VMs.
- Web Application Firewall (WAF) and Azure Firewall: Offer advanced security with application layer protection.
- Local Admin Password Solution (LAPS): Ensures strong local admin passwords and just-in-time access.
📈 Common Segmentation Patterns
Here are a few typical ways to segment your network:
- Single VNet: All resources are within one VNet.
- Multiple VNets with peering: Resources are distributed across several VNets.
- Hub and spoke model: One VNet acts as a hub with other VNets as spokes, providing a central point for connectivity.
Recommendations for networking and connectivity
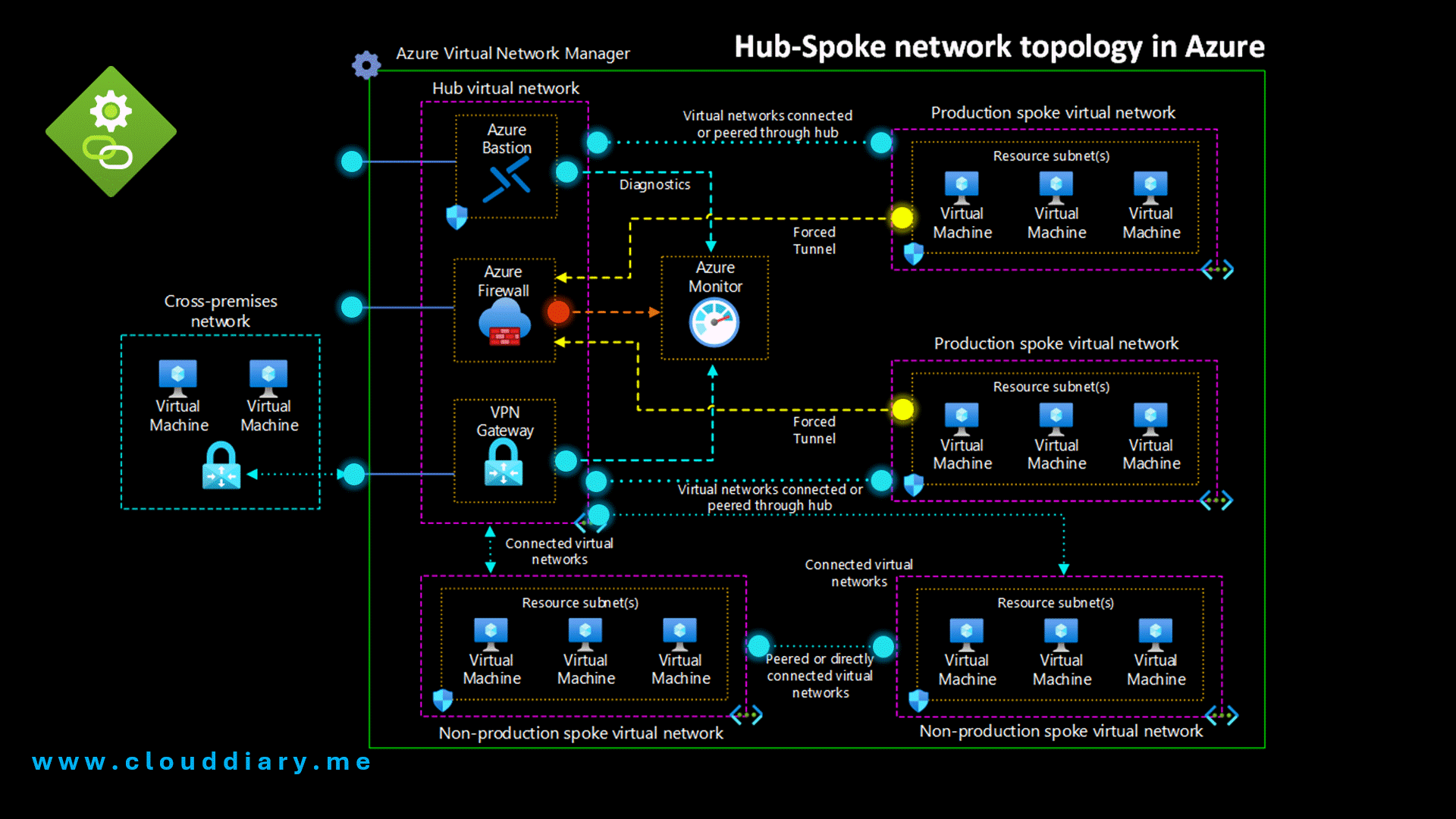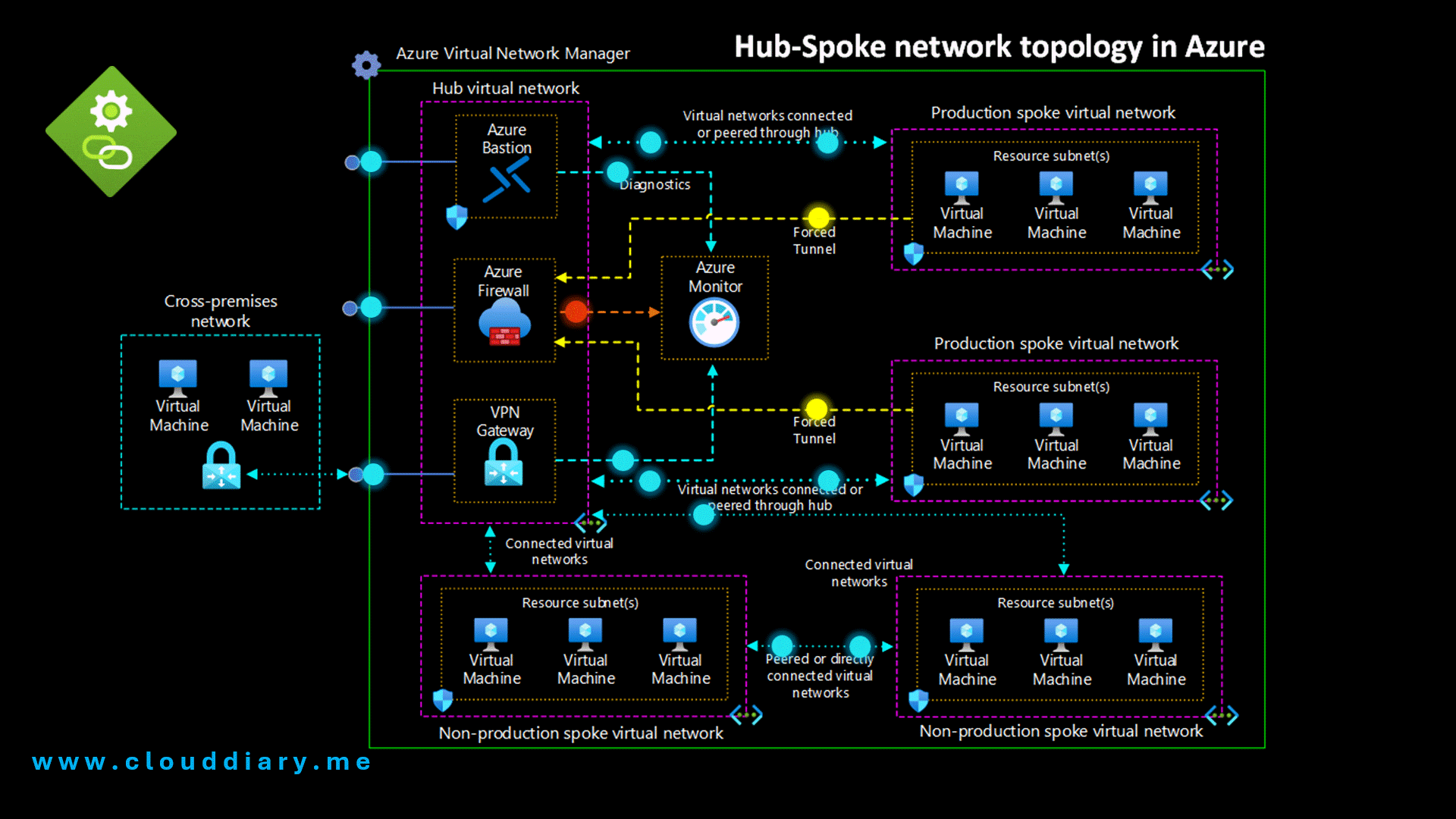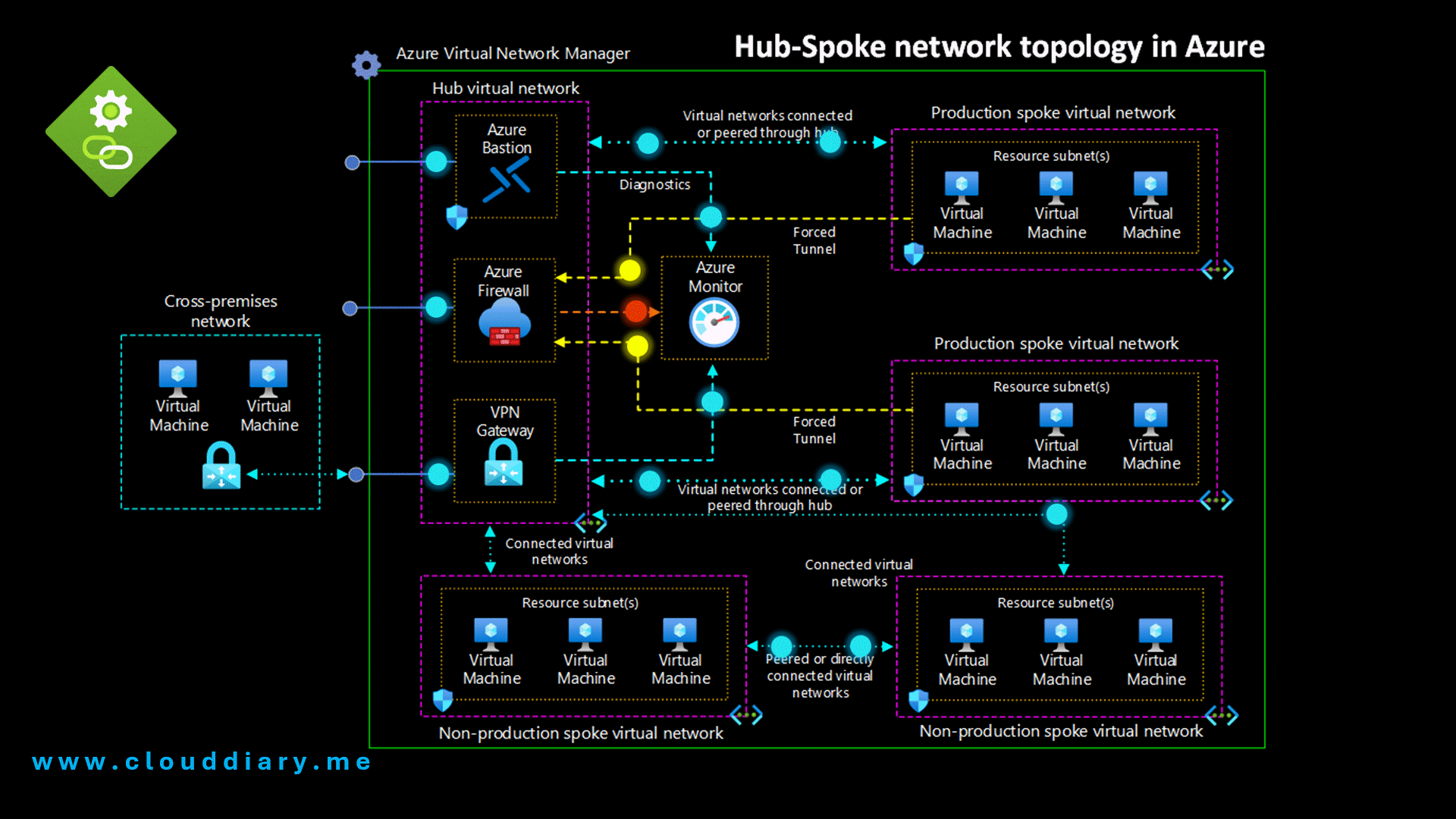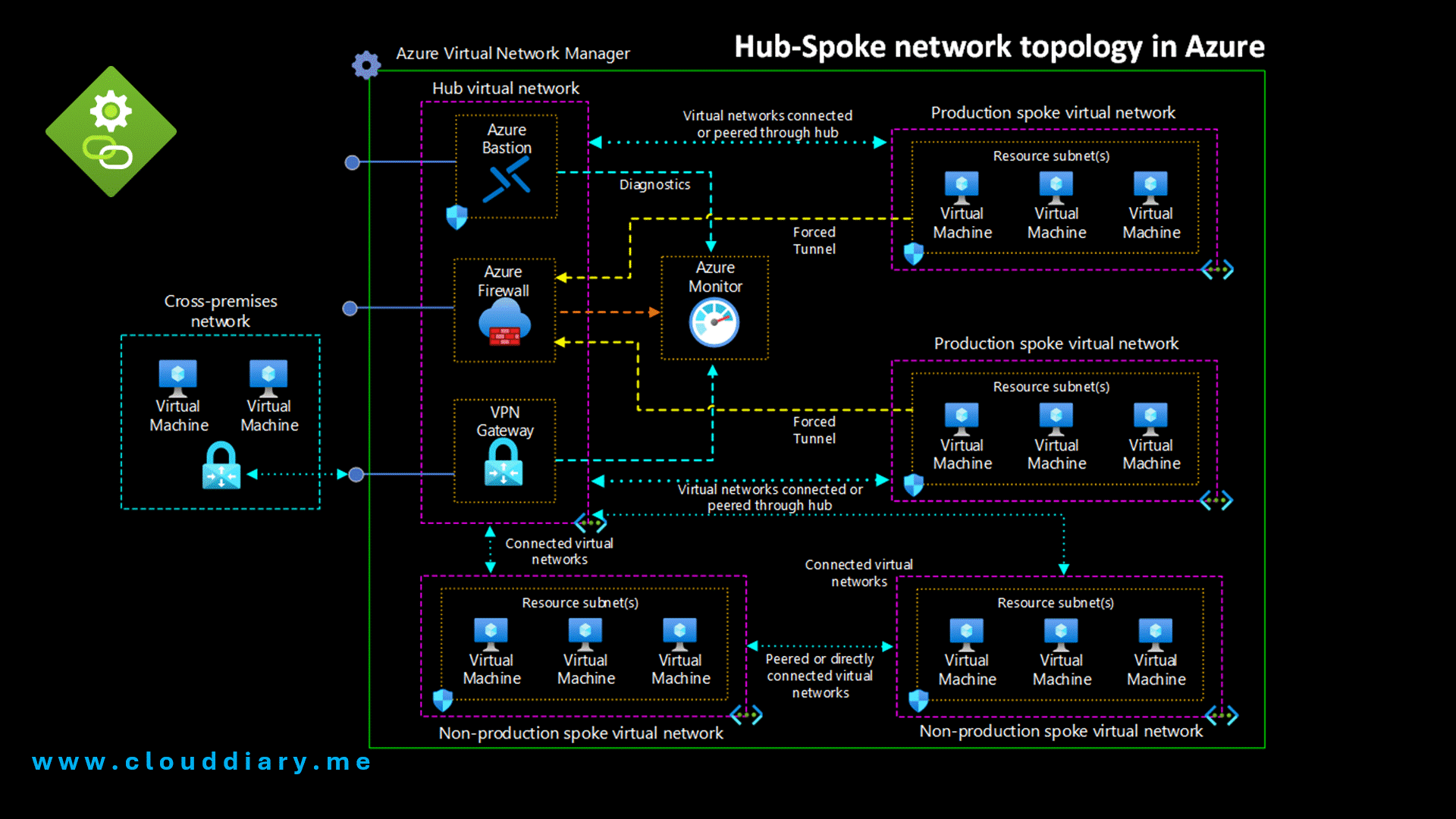
Hub-spoke network topology in Azure
Workflow
This hub-spoke network configuration uses the following architectural elements:
-
Hub virtual network. The hub virtual network hosts shared Azure services. Workloads hosted in the spoke virtual networks can use these services. The hub virtual network is the central point of connectivity for cross-premises networks.
-
Spoke virtual networks. Spoke virtual networks isolate and manage workloads separately in each spoke. Each workload can include multiple tiers, with multiple subnets connected through Azure load balancers. Spokes can exist in different subscriptions and represent different environments, such as Production and Non-production.
-
Virtual network connectivity. This architecture connects virtual networks by using peering connections or connected groups. Peering connections and connected groups are non-transitive, low-latency connections between virtual networks. Peered or connected virtual networks can exchange traffic over the Azure backbone without needing a router. Azure Virtual Network Manager creates and manages network groups and their connections.
-
Azure Bastion host. Azure Bastion provides secure connectivity from the Azure portal to virtual machines (VMs) by using your browser. An Azure Bastion host deployed inside an Azure virtual network can access VMs in that virtual network or in connected virtual networks.
-
Azure Firewall. An Azure Firewall managed firewall instance exists in its own subnet.
-
Azure VPN Gateway or Azure ExpressRoute gateway. A virtual network gateway enables a virtual network to connect to a virtual private network (VPN) device or Azure ExpressRoute circuit. The gateway provides cross-premises network connectivity. For more information, see Connect an on-premises network to a Microsoft Azure virtual network and Extend an on-premises network using VPN.
-
VPN device. A VPN device or service provides external connectivity to the cross-premises network. The VPN device can be a hardware device or a software solution such as the Routing and Remote Access Service (RRAS) in Windows Server. For more information, see Validated VPN devices and device configuration guides.
📝 Creating a Secure Hub and Spoke Network
To get started with a secure hub and spoke network, check out this step-by-step tutorial.
By implementing these best practices, you can build a secure and efficient network on Azure, protecting your organization’s assets and ensuring compliance with governance policies.

