- Home
- Security & Compliance
- Applying the Azure Well-Architected Framework
Applying the Azure Well-Architected Framework
Applying the Azure Well-Architected Framework
A Pillar-by-Pillar Approach for Building Robust Cloud Solutions
Building on the cloud is more than just deploying virtual machines; it’s about crafting solutions that are secure, resilient, efficient, and operationally sound. The Azure Well-Architected Framework provides the blueprint. It’s not a rigid set of rules, but a collection of guiding tenets, organized into five pillars, designed to help you critically evaluate your architecture. Today, I want to write about how applying this framework is a continuous journey, not a one-time checklist, ensuring your cloud solutions are robust and ready for the future.
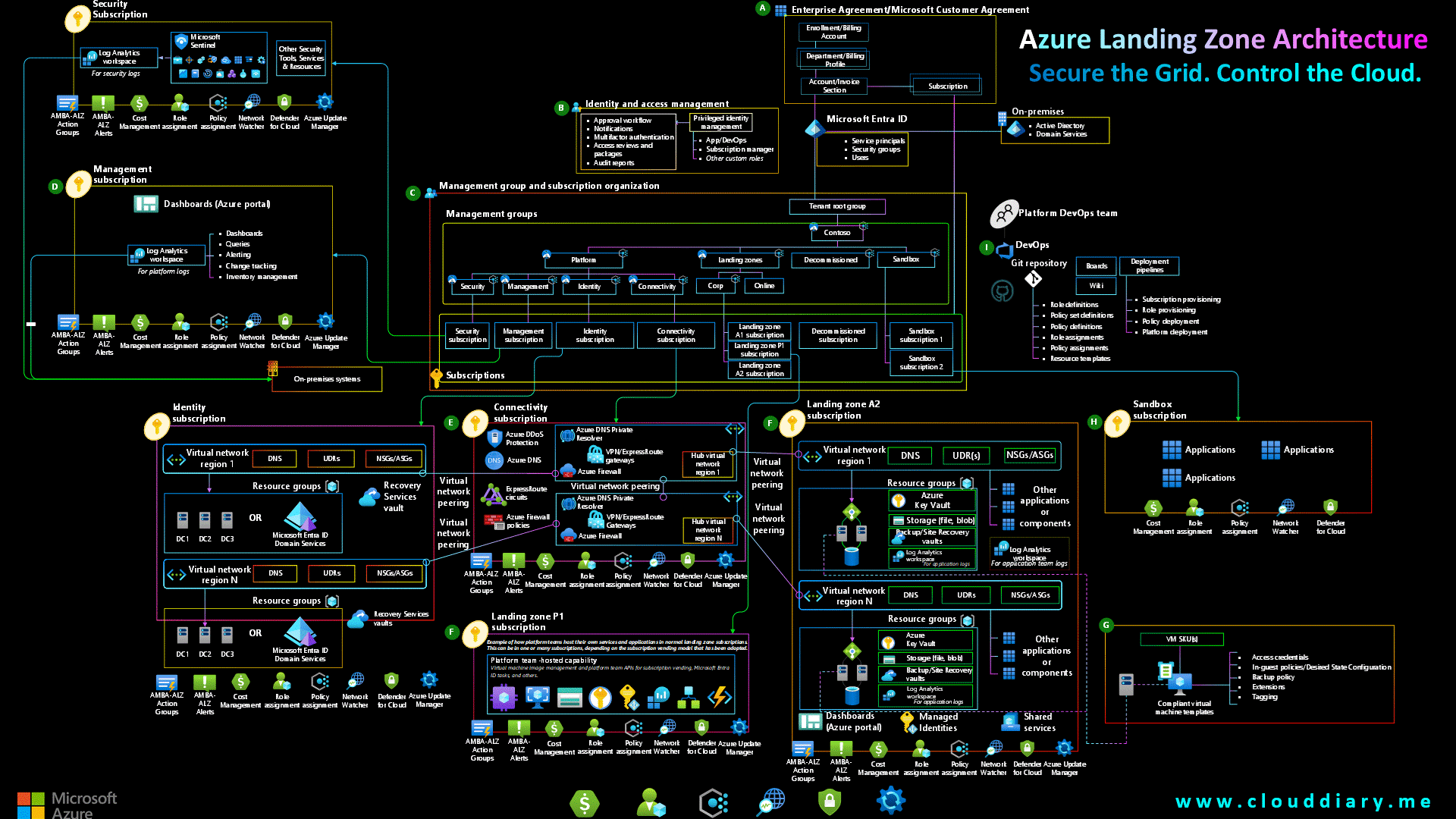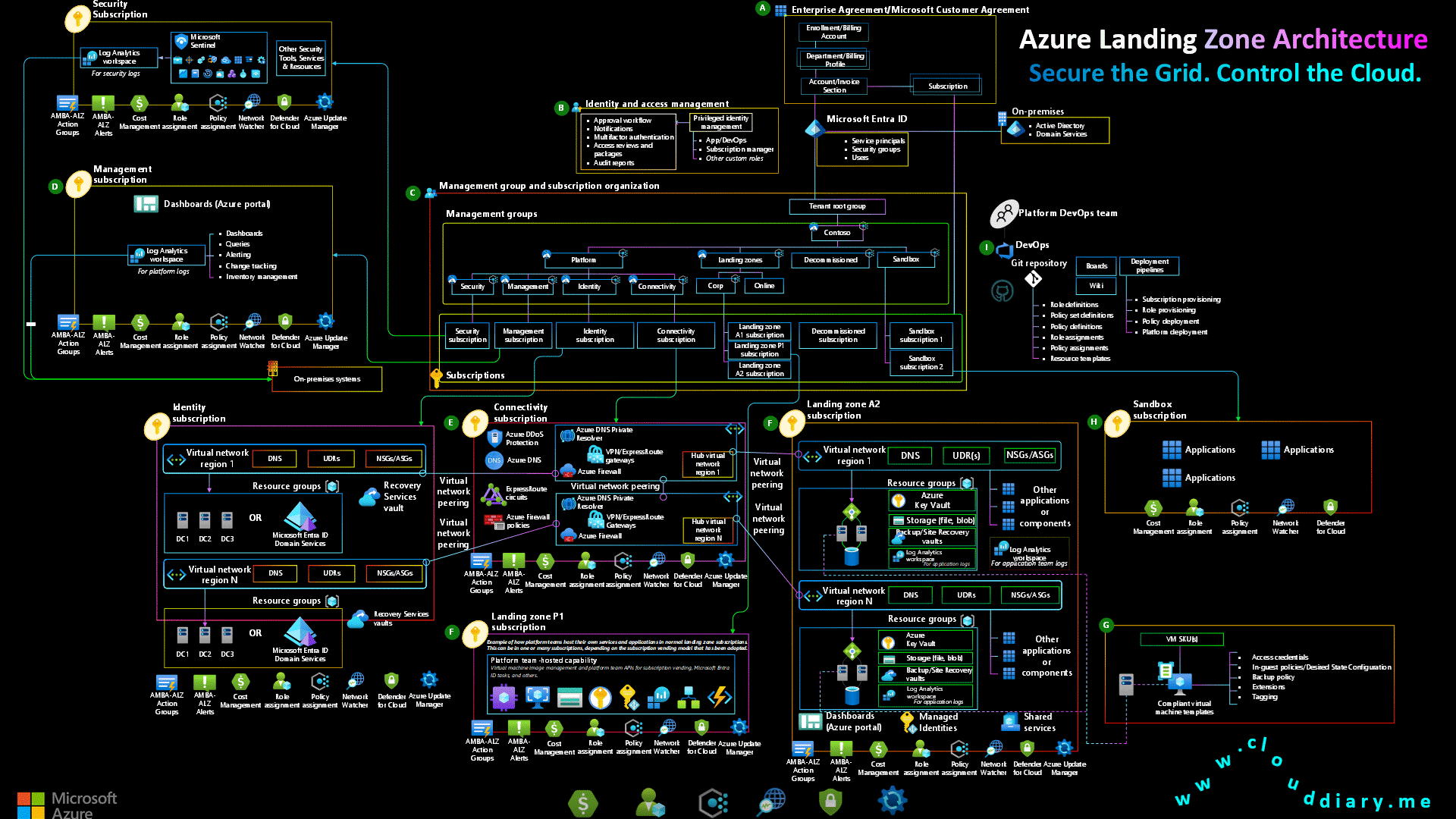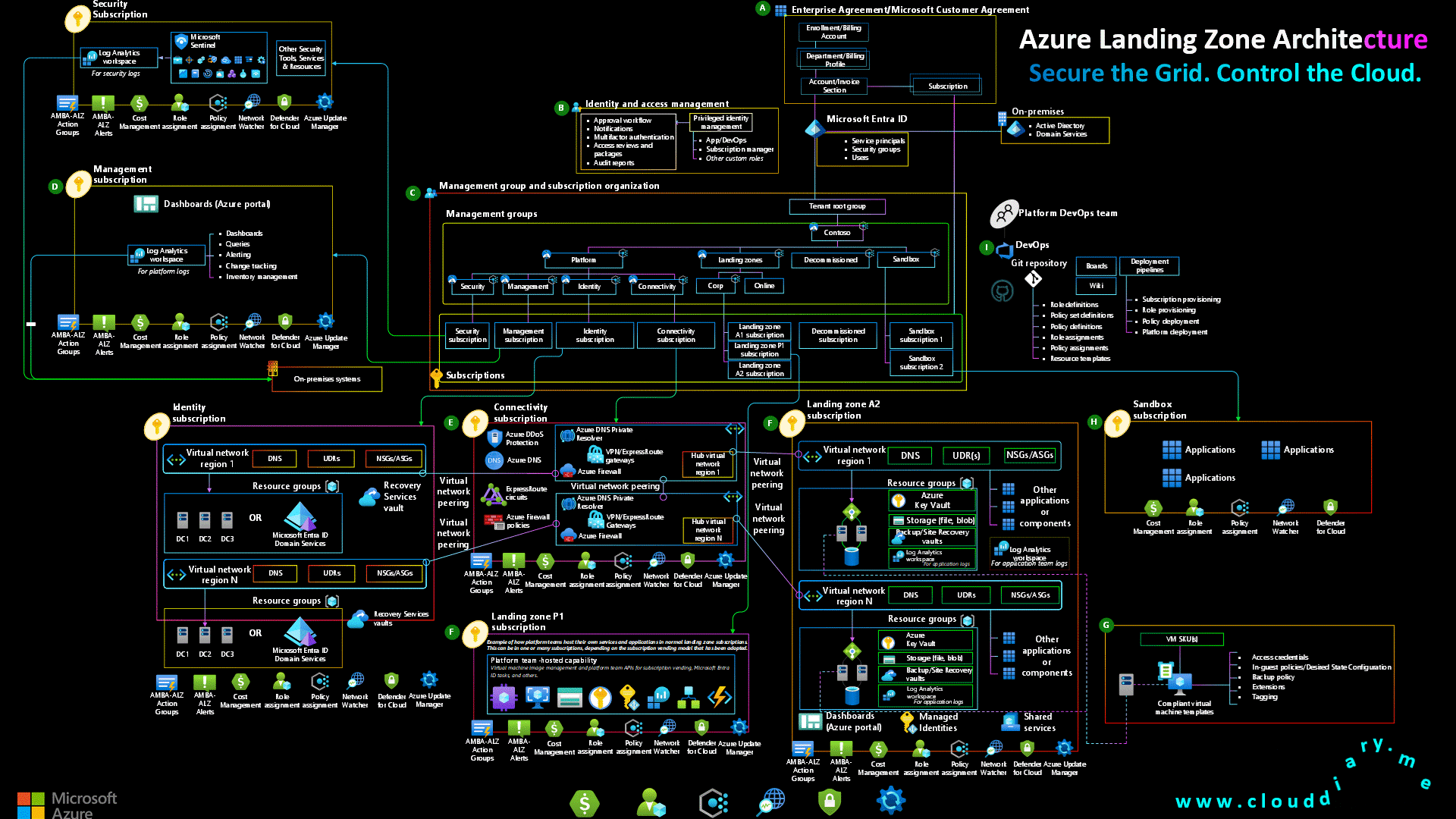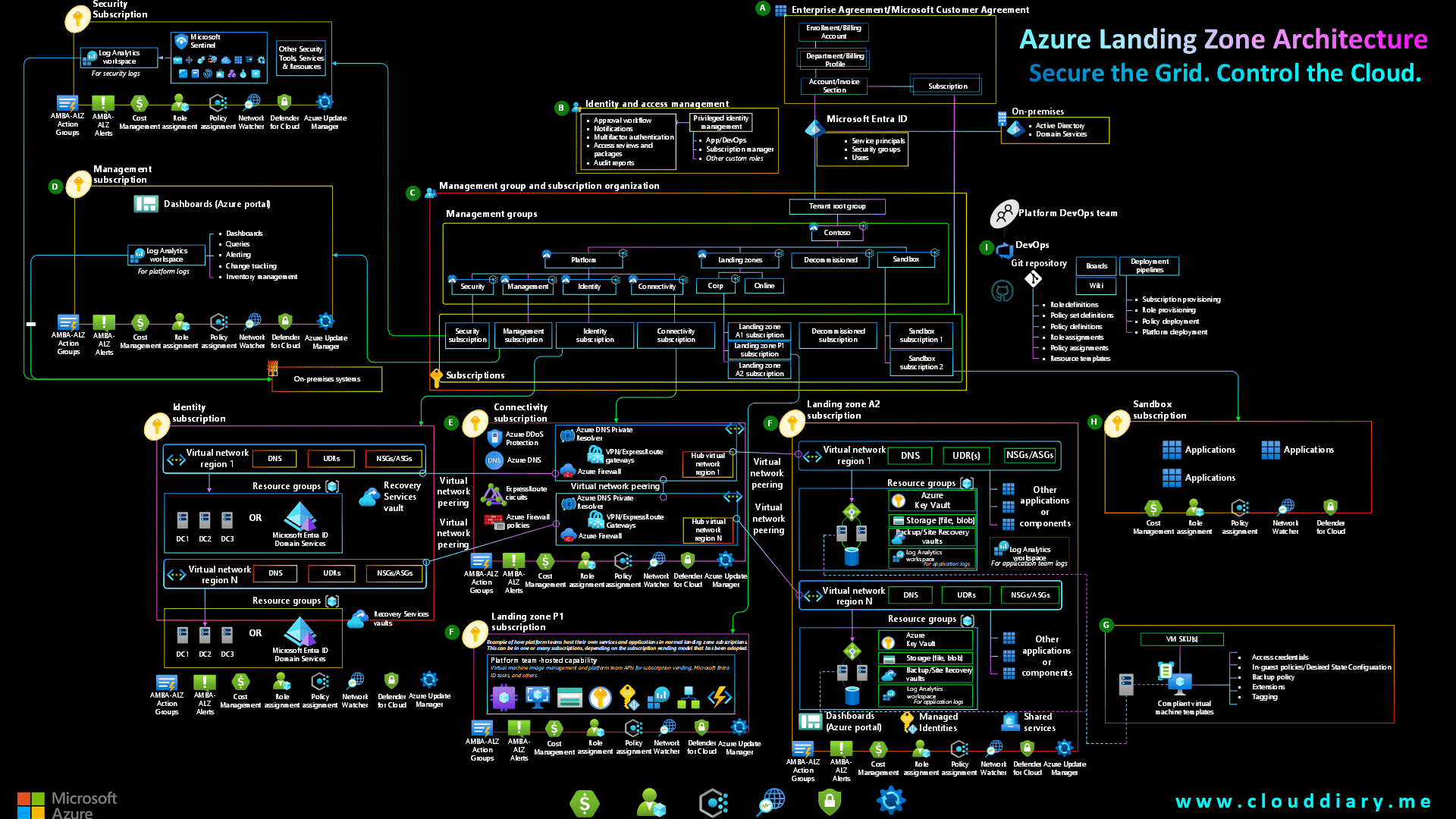
🏗️ Pillar 1: Reliability
"How does your application respond to failure and maintain availability for your users?"
Design for High Availability (HA)
Failures are inevitable; your architecture must anticipate them. For regional resilience, distribute your application components across multiple Availability Zones. Each Zone is a physically separate datacenter within an Azure region, protecting you from localized power, cooling, or networking failures. This is a foundational step for building business-critical applications with a high SLA.
Plan for Disaster Recovery (DR)
High availability protects against small-scale failures, while DR prepares you for large-scale outages, like a whole region becoming unavailable. Define your Recovery Time Objective (RTO) and Recovery Point Objective (RPO) and architect a multi-region DR strategy. Use Azure Site Recovery to orchestrate the replication and failover of your VMs to another region, ensuring business continuity.
Build Self-Healing Applications
A reliable system can recover from transient faults automatically. Design your application code using resilience patterns like the Retry Pattern for temporary network issues and the Circuit Breaker Pattern to prevent a failing service from being repeatedly called. Many Azure PaaS services, like Azure SQL and Storage, have these capabilities built into their SDKs, simplifying resilient design.
🛡️ Pillar 2: Security
"How are you protecting your system from threats and managing user identities?"
Adopt a Zero Trust Model
The old model of a secure network perimeter is obsolete. Assume every request could be a threat. Treat identity as your primary security boundary. Use Microsoft Entra ID to manage all user and service identities. Enforce Multi-Factor Authentication (MFA) universally and apply granular Conditional Access policies to verify every access request based on user, location, device health, and real-time risk.
Implement Defense-in-Depth
Layer your security controls. Segment your virtual networks with Network Security Groups (NSGs) and use Azure Firewall with threat intelligence. For web applications, deploy Azure Application Gateway with WAF to protect against common exploits. Secure sensitive credentials and secrets in Azure Key Vault, never in code or configuration files.
Centralize Security Posture Management
You can't protect what you can't see. Use Microsoft Defender for Cloud as your central dashboard for security posture management across all Azure, hybrid, and even multi-cloud resources. It provides a secure score, regulatory compliance reporting, and threat detection in one place.
💰 Pillar 3: Cost Optimization
"Are you continuously monitoring spend and using the most cost-effective services for your needs?"
Right-Sizing Resources
Cloud waste is often the biggest unnecessary expense. Regularly review your VM sizes, storage tiers, and database performance levels to match actual usage. Use Azure Advisor to get concrete, actionable recommendations for terminating idle resources and right-sizing underutilized ones.
Leverage Azure Pricing Models
Pay-as-you-go is flexible but not always cheapest. For predictable workloads, commit to Azure Reservations or Savings Plans to receive significant discounts. For interruptible workloads, architect to use Azure Spot Virtual Machines for massive savings.
Implement Governance and Tagging
Cost management is a team sport. Use Azure Policy to enforce rules, like allowing only specific VM sizes. Implement a robust tagging strategy to allocate costs to different teams. Use Budgets within Azure Cost Management + Billing to set spending limits and receive automated alerts.
⚙️ Pillar 4: Operational Excellence
"How do you manage, deploy, and monitor your application to ensure smooth, repeatable operations?"
Automate Everything with Infrastructure as Code (IaC)
Manual deployments are slow and error-prone. Define all your Azure infrastructure using Bicep or ARM Templates. Store this code in a Git repository. This makes your environments repeatable, auditable, and easy to tear down and rebuild—the cornerstone of modern DevOps.
Build a Mature CI/CD Pipeline
Automate the path from code commit to production. Use Azure DevOps Pipelines or GitHub Actions to build a robust continuous integration and continuous delivery (CI/CD) pipeline that automatically builds, tests, and deploys your application.
Embrace Comprehensive, Actionable Monitoring
Use Azure Monitor and Application Insights to gain deep, end-to-end visibility into your application's health. Track not just performance but also user behavior and business-level KPIs. Create actionable alerts that trigger automated responses or notify the correct team.
🚀 Pillar 5: Performance Efficiency
"Can your system scale efficiently to handle fluctuations in user traffic and load?"
Implement Smart Autoscaling
Performance is about matching capacity to demand. Most Azure compute services, including VM Scale Sets and App Service Plans, support autoscaling. Configure rules to automatically scale out during peak load and scale in during quiet periods.
Optimize Your Data and Caching Strategy
The slowest part of an application is often the data tier. For globally distributed applications needing low latency, consider Azure Cosmos DB. Implement a caching layer with Azure Cache for Redis to serve frequently accessed data from a fast, in-memory store.
Monitor and Tune Continuously
Use Azure Monitor and Application Insights to collect detailed performance metrics. Analyze this telemetry to identify bottlenecks, whether in CPU, memory, I/O, or application code. Set up performance alerts to proactively identify issues before they impact users.
Hey! Thanks for reading my blog 🙌
If something still feels a bit complex, don’t worry — I’ve got you covered.
Just enter any technical term from this article (like “Zero Trust,” “CI/CD,” or “Availability Zones”), and my AI will explain it in simple, easy-to-understand language.


Senthil Kumar
December 17, 2025Excellent clear explanation.👏👏
Anuradha
December 22, 2025Thank You