- Home
- Security & Compliance
- Blueprint to Get Your Azure Landing Zone Spot-On
Blueprint to Get Your Azure Landing Zone Spot-On
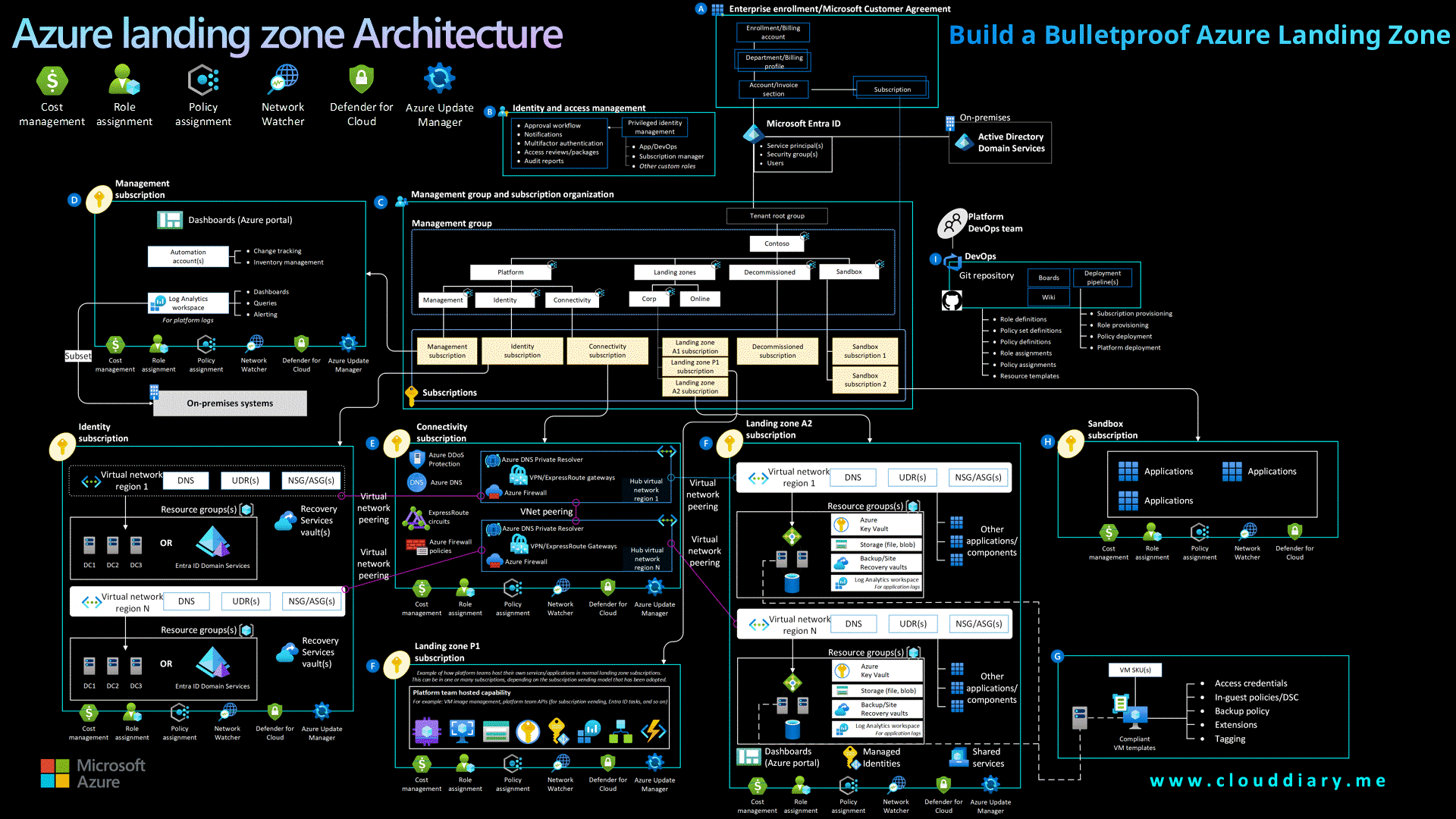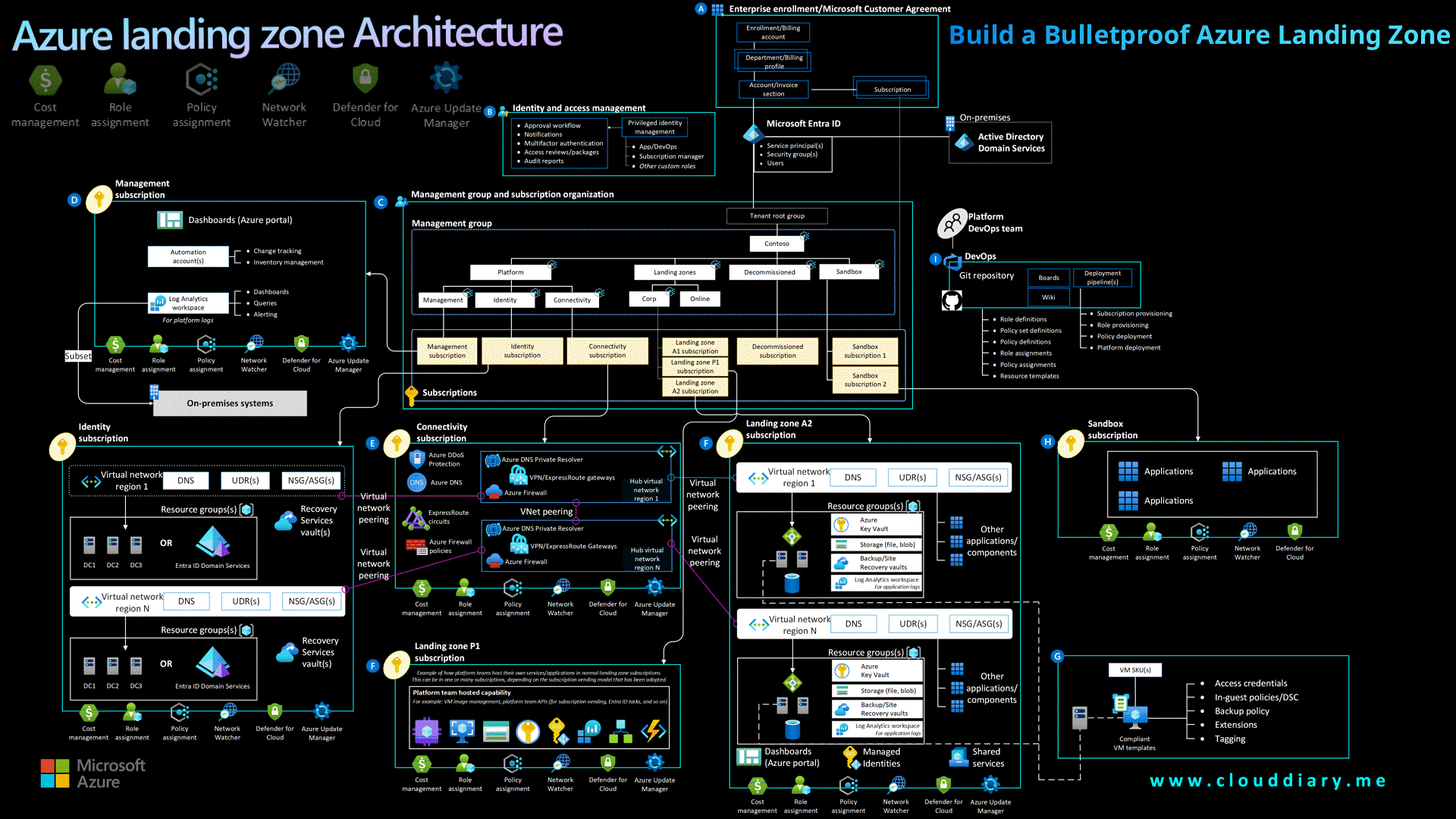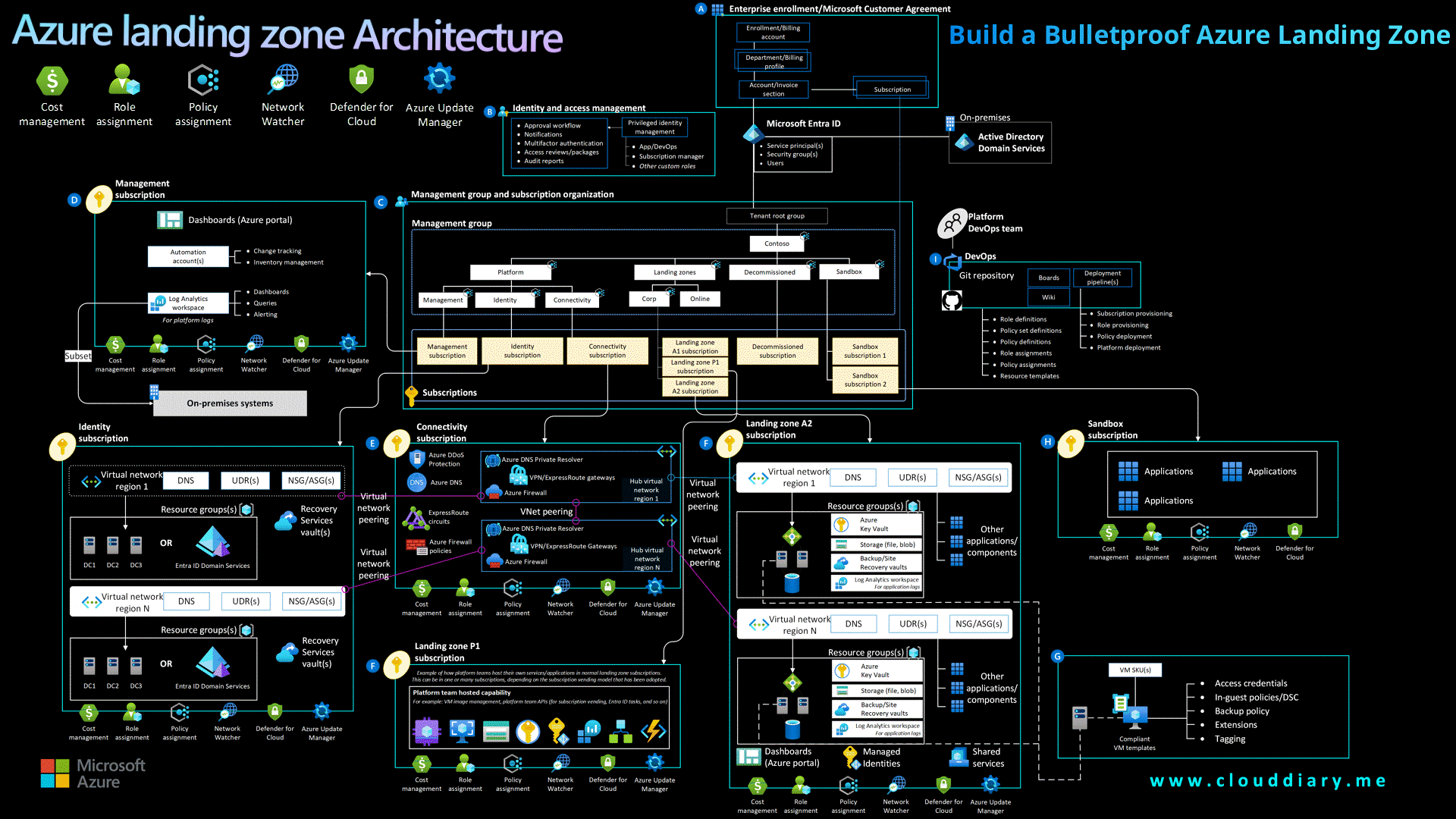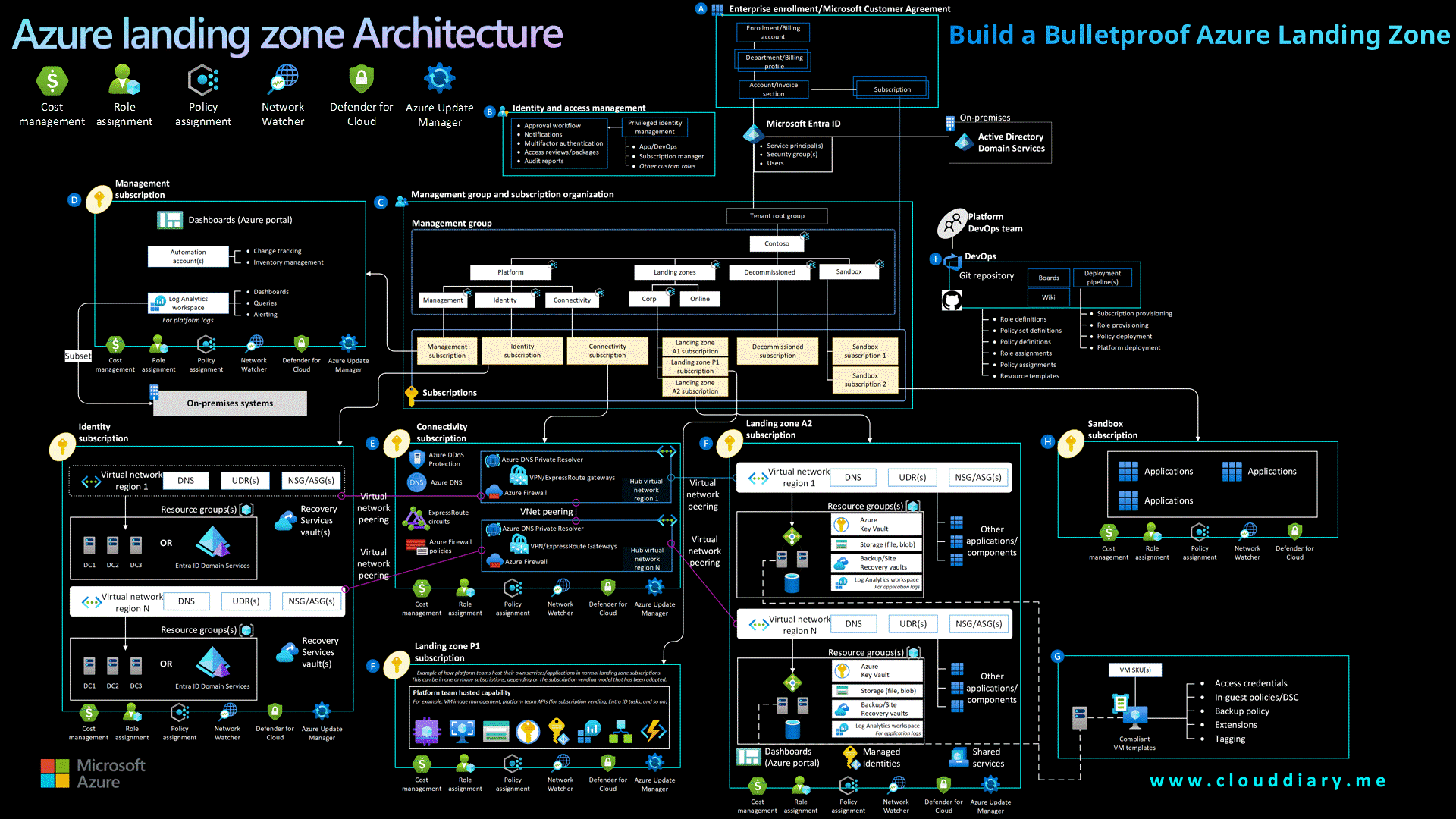
Build a Bulletproof Azure Landing Zone

Because a Wobbly Foundation Breaks Everything
Many organizations rush into Azure, eager to embrace the cloud but skip the groundwork. They focus on getting things running quickly, deploying services and scaling workloads, but neglect the foundational elements like governance, security, and architecture. The result? Ballooning costs, unmanaged access, inconsistent deployments, and increased risk exposure.
This approach might work in the short term, but it rarely holds up as the environment grows. Without a solid Landing Zone, things begin to break under the weight of scale, complexity, and compliance.
Let’s fix that …
Whether you’re starting fresh or improving an existing setup, this guide will help you avoid common pitfalls and build with clarity and confidence.
✅ 1. Know the “Why” Before the “How”
Don’t build tech—build solutions.
Before even touching the Azure portal, ask:
🎯 What are we trying to achieve? (Agility? Innovation? Cost control?)
🔐 What must be protected at all costs? (PII, compliance-critical data?)
🧱 What legacy or critical systems must remain stable?
Clear goals drive clear architecture. Tie every cloud decision to business impact.
🧭 2. Assess Your Starting Point
Are you greenfield (new build) or brownfield (existing footprint) or Lift & Shift (Mostly for On-Prem Customers)?
Greenfield? Start clean with proven design patterns.
Lift & Shift? Move onprem Work loads to the Cloud as it is.
Brownfield? Assess your current setup using tools like Azure Advisor and Well-Architected Review. Find the gaps before scaling up.
Use Azure Landing Zone Accelerator as a baseline, it provides modular, production-ready architecture tailored to Microsoft best practices.
🛡️ 3. Apply Governance Early, Not Eventually
Don’t treat governance as cleanup bake it into the design.
PIM & PAM:
PIM (Privileged Identity Management): Just-in-time access to reduce attack surface.
PAM (Privileged Access Management): Protect sensitive resources with controlled workflows.
RBAC: Grant the least privilege—no more, no less. Avoid custom roles unless necessary.
Tags: Standardize them early (e.g.,
Environment,Owner,CostCenter) and enforce via Azure Policy.Azure Policy & Blueprints: Automate enforcement for compliance, naming, and security. (Blueprints are legacy; migrate to Custom Policy Initiatives.)
🌐 4. Design a Secure, Scalable Network
Your network is the cloud’s nervous system. Build it right from day one.
Use Virtual WAN or Hub-Spoke topology for scaling.
Deploy NSGs (Network Security Groups) and ASGs (Application Security Groups).
Use Private Endpoints to eliminate public exposure.
Leverage Azure Firewall, DDoS Protection, and Web Application Firewall (WAF) where needed.
🧱 5. Automate Everything: Deployment the Smart Way
Manual clicks don’t scale.
Use Infrastructure as Code (IaC):
Choose Bicep, ARM templates, or Terraform.
Store code in Azure DevOps or GitHub with pull request reviews.
Implement CI/CD pipelines for repeatable, testable deployments.
🔐 6. Identity: The New Security Perimeter
In the cloud, identity is the perimeter. Secure it like a vault.
Use Entra ID (formerly Azure AD) for identity governance.
Block legacy protocols (POP, IMAP).
Enable MFA by default, especially for admins.
Monitor risky sign-ins with Microsoft Entra Identity Protection.
Review permissions with Access Reviews regularly.
📊 7. Set Up Monitoring and Insights from Day Zero
You can’t fix what you can’t see.
Use Azure Monitor, Log Analytics, and Azure Metrics Explorer.
Enable Diagnostic Settings for all key resources.
Use Application Insights for deep app telemetry.
Create workbooks and dashboards for real-time visibility.
🧪 8. Test Environments Are Not Optional
Never deploy blind.
Use staging or UAT environments to test templates, role assignments, and policies.
Automate testing with tools like PSRule for Azure or Terraform Sentinel.
Simulate cost scenarios with Azure Pricing Calculator or Cost Management + Billing.
🔒 9. Run a Final Security and Compliance Sweep
Before go-live, run through this checklist:
✅ Encryption in place (at rest + in transit)?
✅ Defender for Cloud recommendations applied?
✅ Just-in-time VM access enabled?
✅ Key vaults secured with firewall rules and access policies?
✅ Regulatory standards met? (ISO, HIPAA, GDPR, etc.)
💰 10. Keep an Eye on Costs (Hello, FinOps!)
Cloud costs don’t bite—they bleed slowly.
Set budgets and alerts in Cost Management.
Use Reserved Instances and Savings Plans where possible.
Review and right-size regularly.
Tag resources with
CostCenterandProject.
FinOps isn’t just finance it’s about cloud accountability.
Final Thoughts: More Than a Checklist
An Azure Landing Zone isn’t just technical scaffolding—it’s your blueprint for cloud success.
✅ Built for scale
✅ Governed for security
✅ Designed with business goals in mind
Whether you’re just starting or course-correcting, this checklist brings clarity to the chaos. Don’t build blindly. Build boldly and land safely.

